Intelligence Requirements
Intelligence Requirements
Assalamo Alaykom Friends , Welcome to another blog in our series on Threat Intelligence. After covering the fundamentals of Cyber Threat Intelligence (CTI), today we’ll dive into the first stage of the intelligence cycle: Planning and Direction. As we’ve explained before, this stage involves several key processes such as defining intelligence requirements and threat modeling.In today’s blog, we will focus on explaining intelligence requirements in detail.
What Are Intelligence Requirements ?
Intelligence requirements (IRs) can be defined as the objectives set by an organization that guide the collection, analysis, and production of intelligence. These objectives define the organization’s priorities in terms of intelligence needs, while also addressing the knowledge gaps that need to be filled.
The main goal of setting intelligence requirements is to understand what types of information are important for a given organization (for example, which types of intelligence the organization wants to collect).
Threat Intelligence without IRs ?
Working with effective intelligence means reinforcing the security posture, proactively monitoring threats, and responding quickly to incidents. However, these fundamental concepts in the world of Cyber Threat Intelligence (CTI) can sometimes not be fully realized if clear intelligence requirements are not properly set up.
What often happens is that some organizations misunderstand the intelligence process. They start by gathering every available Indicator of Compromise (IOC), subscribing to all threat feed vendors, and then dumping this data into their SIEM. This approach results in numerous useless alerts and false positives, overwhelming the security team and ultimately reducing overall effectiveness. Properly defined intelligence requirements are essential to filter relevant data, guide collection efforts, and enhance decision-making.
We have to remember that there is no universal intelligence that works for every organization. Each organization must align its threat intelligence processes with its own specific profile. For example, an organization using a particular type of technology will focus more on producing and collecting intelligence related to that technology, rather than on a technology they don’t use.
By aligning intelligence efforts with their specific needs, organizations can avoid unnecessary noise and help their security teams focus on relevant threats.
Examples of Intelligence Requirements
When defining threat intelligence requirements, the process begins with formulating a set of questions that align with the organization’s specific intelligence needs. The answers to these questions then serve as a guide for the entire intelligence cycle, helping to focus efforts on gathering, analyzing, and disseminating relevant and actionable intelligence.
examples :
- Who will consume the threat intelligence?
- What assets do we need to defend?
- What threats is our industry facing?
- What threats is our geographic area facing?
Types of Intelligence Requirements
When it comes to Intelligence Requirements (IR) types, there are three main categories :
- High-Level Requirements: Strategic needs defining which threat actors, business sectors, and regions the organization focuses on.
- Example: The organization is concerned with nation-state actors targeting its financial services in North America and Europe.
- Functional Requirements: Technical needs related to the organization’s infrastructure and security focus.
- Example: The organization uses a mix of Windows servers and cloud-based systems and requires intelligence to defend against ransomware and phishing attacks.
- Capability/Visibility Requirements: Data and tools the organization needs for internal visibility to meet high-level and functional requirements.
- Example: Access to email logs, firewall logs, DNS data, and endpoint visibility to detect and respond to threats like phishing and unauthorized access.
Priority Intelligence Requirements (PIRs) : are key intelligence needs that help an organization focus on the most important information to address critical risks or threats. They guide intelligence collection efforts, ensuring resources are used effectively to support decision-making and improve security.
Developing Priority Intelligence Requirements
To provide a well-explained example, I will follow the process for developing Priority Intelligence Requirements (PIR) as outlined by Ondra Rojčík in the Red Hat process.
The Red Hat process :
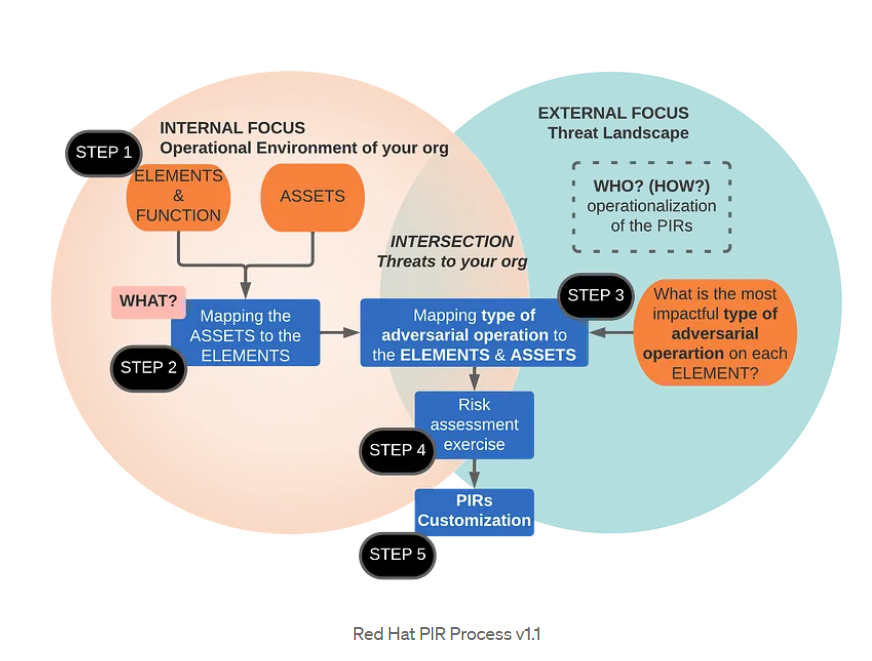
This image presents the process of developing Priority Intelligence Requirements (PIRs) according to Red Hat, which consists of 5 steps:
Step 1: Extracting Organization Elements :
Defining these elements helps in establishing your organization’s identity.
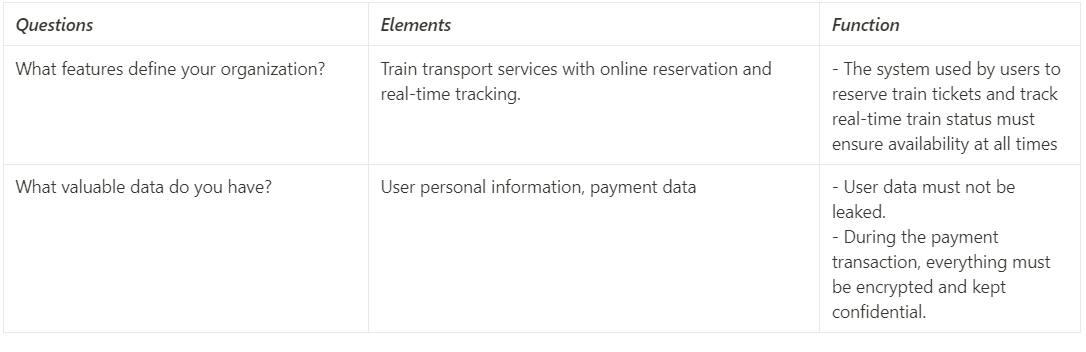
- What features define your organization?
- What makes your organization unique?
- What are the key aspects of your strategy?
- Why are people buying your products/services?
- What is your competitive advantage?
- Are certain products or services more important than others?
- What valuable data do you have?
This step also contains a sub-step called Function, which specifies what elements need to be secured from an information security standpoint.
Step 2: Assets Mapping to Elements :
An asset may be tangible (e.g., a physical item such as hardware, firmware, computing platform, network device, or other technology components) or intangible (e.g., humans, data, information, software, capability, function, service, trademark, copyright, patent, intellectual property, image, or reputation).
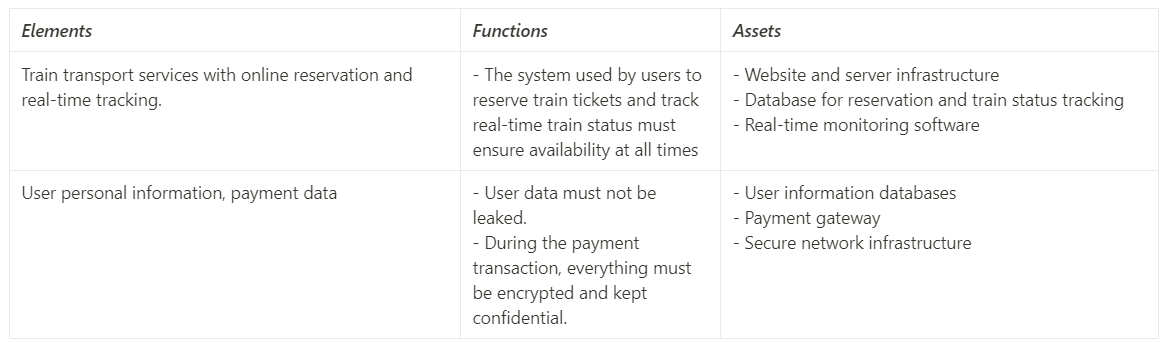
Once you have defined your organization elements, the next step is to map the supporting technology, data, or information to these elements.
Link the abstract elements of your organization (such as strategies, functions, or objectives) to tangible assets (such as infrastructure, data, and technology).
Step 3: Linking Elements with Types of Adversarial Operations :
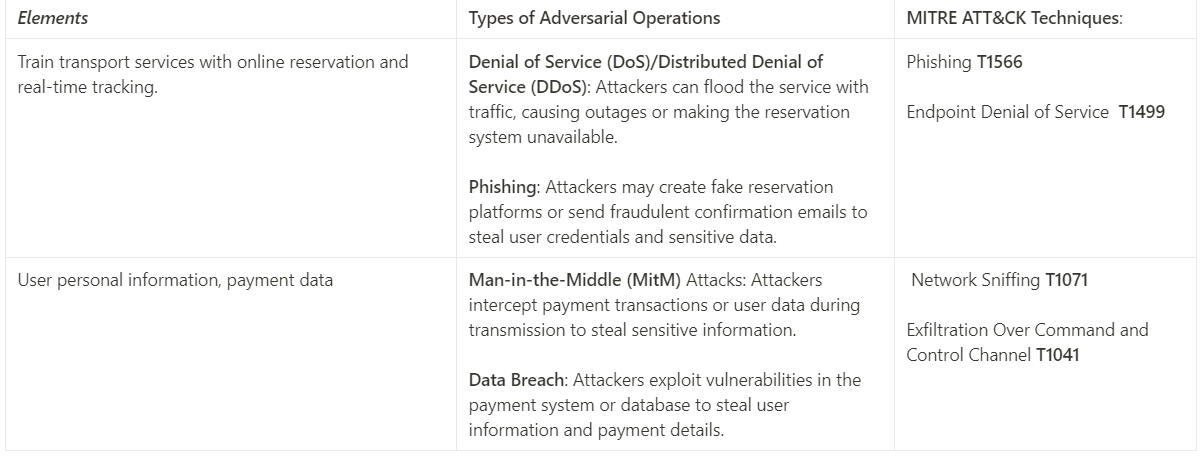
- This step involves connecting the previously identified organizational elements (from Step 1) with specific types of adversarial operations.
- The classification focuses on the impact of cyberattacks on business operations, helping the organization identify which threats are most relevant and damaging.
- This step is necessary to ensure the terms used in the classification are applicable in threat intelligence platforms (TIPs), which is vital for operationalization and effective threat intelligence gathering.
- We may also use frameworks such as MITRE ATT&CK to map adversarial tactics and techniques to the organization’s elements, providing a structured way to understand how specific threats can impact the business.
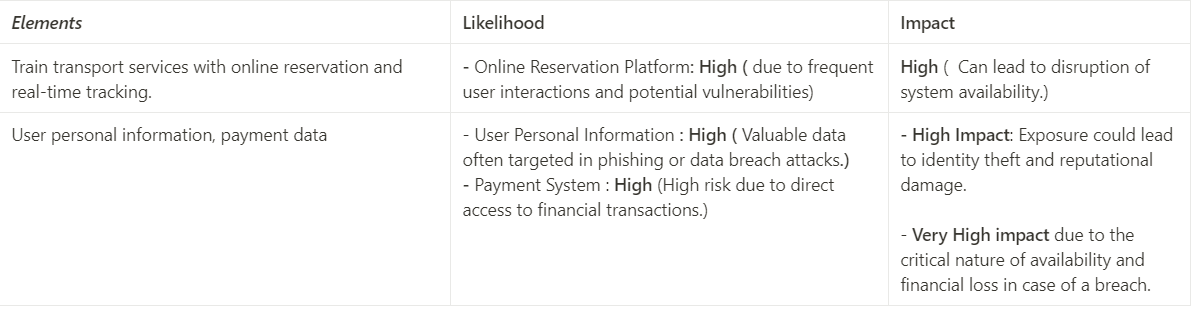
STEP 4: Risk Assessment Using Likelihood/Impact Matrix
- The fourth step involves a risk assessment exercise using a likelihood/impact matrix.
- Likelihood: How appealing are the organization’s elements as targets for attackers? This involves determining the attractiveness of an element or asset to attackers and the potential consequences of a compromise.
- Impact: What would be the worst-case scenario if an attacker compromised these assets? This assesses the severity of the damage to the organization.
STEP 5 Customization of the PIRs :
At the end of the risk assessment, you’ll have a ranked list of key elements mapped to adversarial operations, which can be used to generate intelligence that meets the specific needs of the organization.
Practical Example of Developing PIRs : We will develop PIRs for an organization providing train transport services. I will define just two elements so that the blog remains concise and you can better understand the concept of this model.
Step 1: Extracting Organization Elements :
Step 2: Assets Mapping to Elements :
Step 3: Linking Elements with Types of Adversarial Operations :
STEP 4: Risk Assessment Using Likelihood/Impact Matrix
STEP 5 Customization of the PIRs :
Based on this matrix, we can set the ranking of these elements.
And with that, we come to the end of this article. Thank you for reading! We’ll catch you in the next blog, where we will delve deeper into the concept of threat modeling, Insha’Allah.
References :