Threat Intelligence Fundamentals
Threat Intelligence Fundamentals :
Hello friends, and welcome to a new blog!
I’ve decided to start a blog series on Cyber Threat Intelligence, where I’ll explore key topics in the field. To provide a solid foundation for the upcoming posts, I’ll begin by detailing the fundamentals of Cyber Threat Intelligence, which will be the focus of this blog.
1-The Thing Called Intelligence
Intelligence can be defined as the process of collecting and processing information about a competitive entity and its agents, which is necessary for an organization or group’s security and well-being.
2-Intelligence & Cybersecurity
In the context of cybersecurity, Threat Intelligence refers to the analysis of information related to the hostile intent, capabilities, and opportunities of an adversary, aimed at addressing specific security requirements. It provides answers to critical questions such as:
- Who: Identifies the adversaries or threat actors.
- What: Focuses on their capabilities and infrastructure.
- Where: Details the industries or sectors being targeted.
- When: Considers the timeliness and timing of the threat.
- Why: Examines the motives and intent behind the attack.
- How: Analyzes adversary behaviors, attack patterns, and techniques.
Additionally, effective threat intelligence must adhere to four key properties, summarized by the acronym CART:
- Completeness: The intelligence should be comprehensive and cover all necessary aspects of the threat.
- Accuracy: The information provided must be precise and reliable.
- Relevance: The intelligence should be pertinent to the organization or security context.
- Timeliness: It must be delivered in a timely manner to ensure effective threat mitigation.
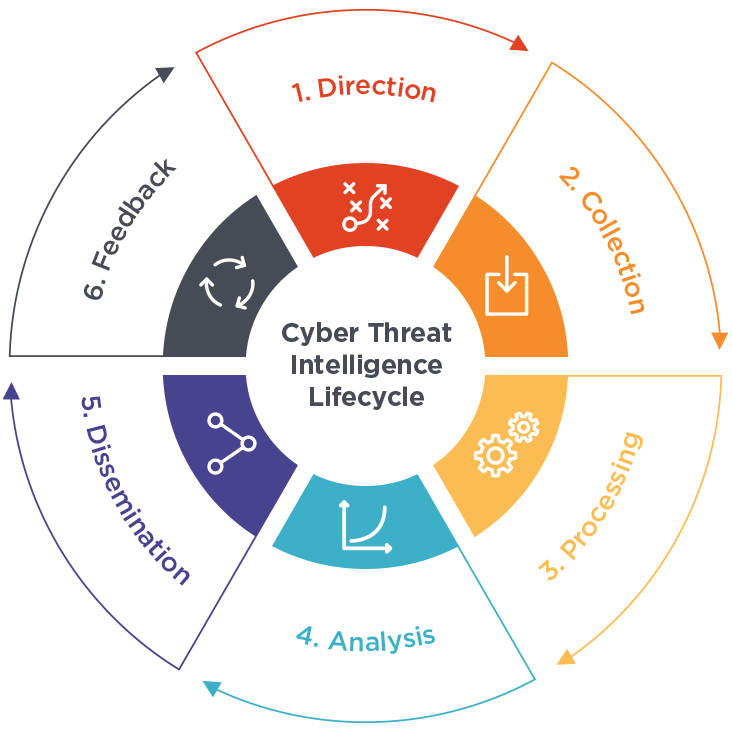
3-The Threat Intelligence Cycle :
The threat intelligence cycle is a structured and continuous process of producing actionable cyber threat intelligence from raw data through processing and analysis.
Planning and Direction Fundamentals :
In this phase, intelligence analysts set the objectives they aim to achieve through the threat intelligence program. Key tasks include:
- Identifying key stakeholders who will receive the threat intelligence.
- Establishing intelligence requirements by understanding what valuable assets within the organization adversaries might target.
- Defining the scope and key objectives of the intelligence program.
- Prioritizing the assets and areas you want to protect.
- Identifying and addressing gaps in current intelligence, such as missing or insufficient information. If strategic goals change or previous CTI efforts highlight gaps, resolve them by gathering new data, refining analysis techniques, or improving distribution methods.
Data Collection :
Once planning is complete, the next step is data collection, where we identify threat intelligence sources that will meet our established requirements.
These sources include: Open Source Intelligence (OSINT), Dark Web Intelligence, Commercial Threat Intelligence Feeds, and Internal Intelligence, such as intrusion analysis reports and security logs.
Processing :
The collected data must be processed to make it suitable for analysis. This involves cleaning, normalizing, and structuring the data by removing duplicates and irrelevant information. Additionally, it includes data enrichment and contextualization, meaning adding context to the data to enhance its relevance and usability.
Analysis & Production :
The processed data undergoes rigorous analysis to identify patterns and potential threats. For example, analysts can use Structured Analytic Techniques (SATs), a method designed to improve the evaluation of information while minimizing bias. The primary goal is to answer the key question: What are the potential threats?
Intelligence Dissemenation :
The threat intelligence is shared with relevant stakeholders, including security teams and incident response teams.
Application :
The organization utilizes threat intelligence to make decisions that enhance security, such as updating security policies and deploying new security measures.
Feedback :
Gather feedback on the effectiveness of the measures implemented. This feedback is used to enhance the threat intelligence cycle for future applications.
4-Types of Threat Intelligence
Threat intelligence can be categorized into three main types: strategic, operational, and tactical.
Strategic threat intelligence provides high-level insights into potential threats and risks facing an organization. It contextualizes these threats within a business framework, assessing their strategic implications and aiding in risk management and organizational decision-making. Key stakeholders include security leaders and organizational executives.
Example: A report highlighting an increase in phishing attacks and supply chain vulnerabilities, allowing organizations to adapt their security strategies accordingly.Operational threat intelligence delivers detailed information about specific threats targeting an organization. It focuses on the tactics, techniques, and procedures (TTPs) employed by threat actors. Key stakeholders include threat hunters, incident response teams, and security leadership.
Example: Insights into TTPs used by attackers.Tactical threat intelligence encompasses technical indicators and behavioral patterns that guide network-level actions and remediation efforts. Stakeholders in this category include security operations teams, network defenders, and incident response personnel.
Example: Indicators of Compromise (IOCs) that help identify and mitigate threats.
And with that, we come to the end of this article. Thank you for reading! We’ll catch you in the next blog, where we will delve deeper into other concepts, Insha’Allah.
References :